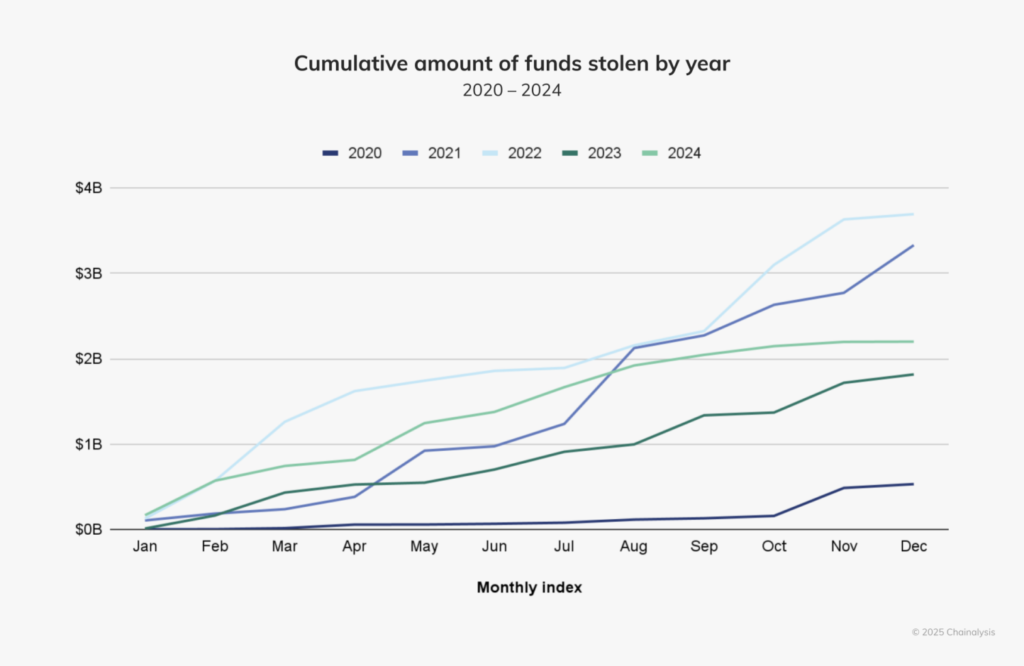
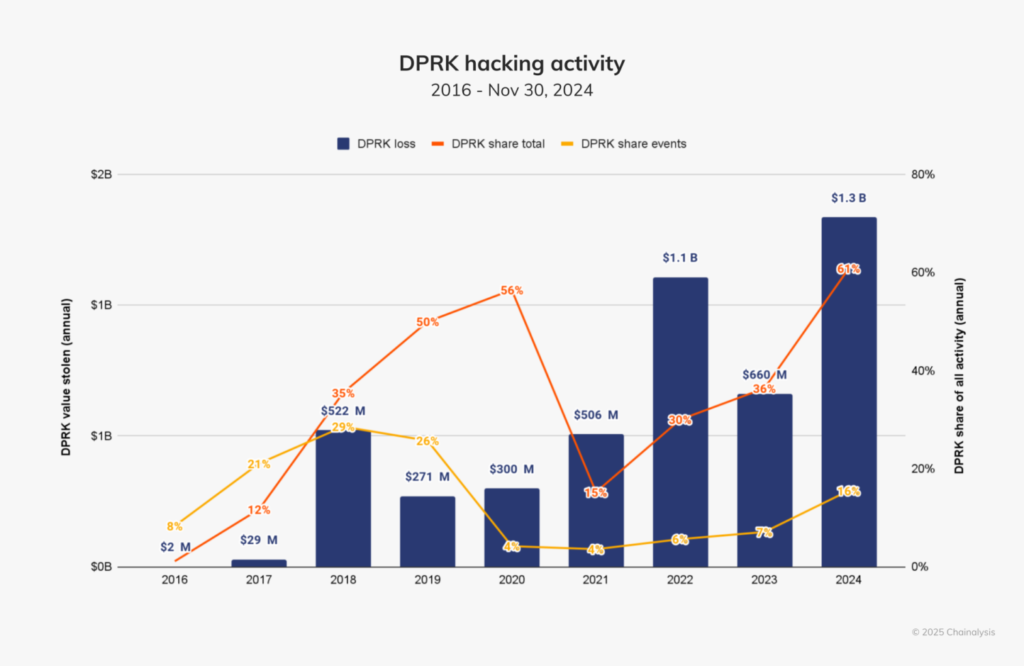
Hackers linked to North Korea escalated their operations in 2024, stealing $2.2 billion in crypto, a 21% increase from 2023. These figures mark the fifth year in the last decade, where crypto theft exceeded $1 billion.
Chainalysis’s recent report shows alarming trends in the year. By July, thefts had reached $1.58 billion, up 84.4% from the same period in 2023.
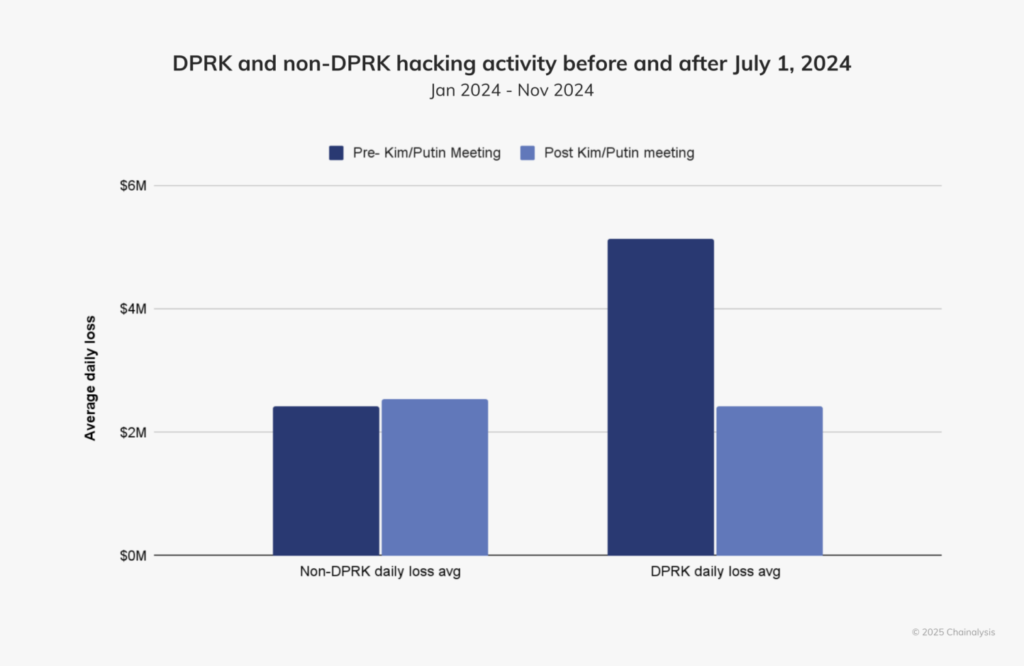
However, by the second half of this year, activities had significantly pulled down to a crawl, with different geopolitical events, such as last June’s summit between Vladimir Putin and Kim Jong Un. The number of funds stolen by DPRK hackers went down by 53.73% after the meeting, which could prove changes in the nation’s cyber priorities.
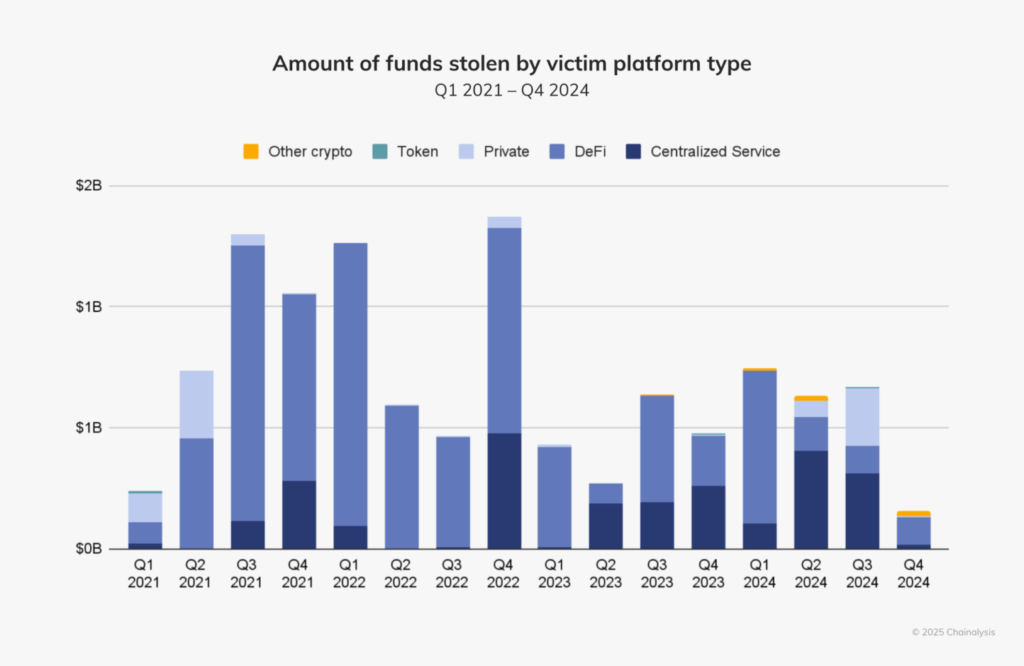
Early in the year, the targets were mainly decentralized finance platforms, but in Q2 and Q3, they became centralized services. A few more notable breaches included a hack on DMM Bitcoin in May, which saw thieves make off $305 million, and a $234.9 million heist from WazirX in July. These incidents underscored vulnerabilities in private key management, which accounted for 43.8% of all crypto theft in 2024.
Crypto laundering tactics evolve with DPRK hacks
North Korea’s cybercrime efforts appear strategic. In 2024, DPRK-linked hackers were responsible for 61% of total stolen crypto, amounting to $1.34 billion across 47 incidents. The average size of their exploits grew, with attacks over $100 million becoming more frequent. The stolen funds reportedly fuel Pyongyang’s missile programs, raising global security concerns.
Tactics have also evolved. North Korean operatives infiltrated Web3 firms, using false identities to access systems. The U.S. Department of Justice recently indicted 14 DPRK nationals who posed as remote IT workers, generating $88 million through corporate espionage and extortion.
The crypto space, even with declining activities in the latter part of the year, is still quite vulnerable to such attacks. The recent $305 million DMM Bitcoin breach did show just how much risk a centralized platform faces. It underscored the dangers of compromised private keys. Many stolen funds have been laundered via mixing services and cross-chain bridges, complicating recovery efforts.
Firms are trying to combat these with predictive tools like those from Hexagate, which apply machine learning as a method of detecting active exploits. These kinds of remedies may be very important in working against such a sophisticated adversary that is relentless.