Since April 2024, the crypto ransomware-as-a-service group Embargo has risen quickly in the cybercrime arena. Analysts link the group to about USD 34.2 million in related transactions. Most victims are in the United States, especially in healthcare, business services, and manufacturing.
Targets include American Associated Pharmacies, Memorial Hospital and Manor in Georgia, and Weiser Memorial Hospital in Idaho. Some ransom demands have reached USD 1.3 million. Evidence suggests Embargo may be a rebranded form of BlackCat.
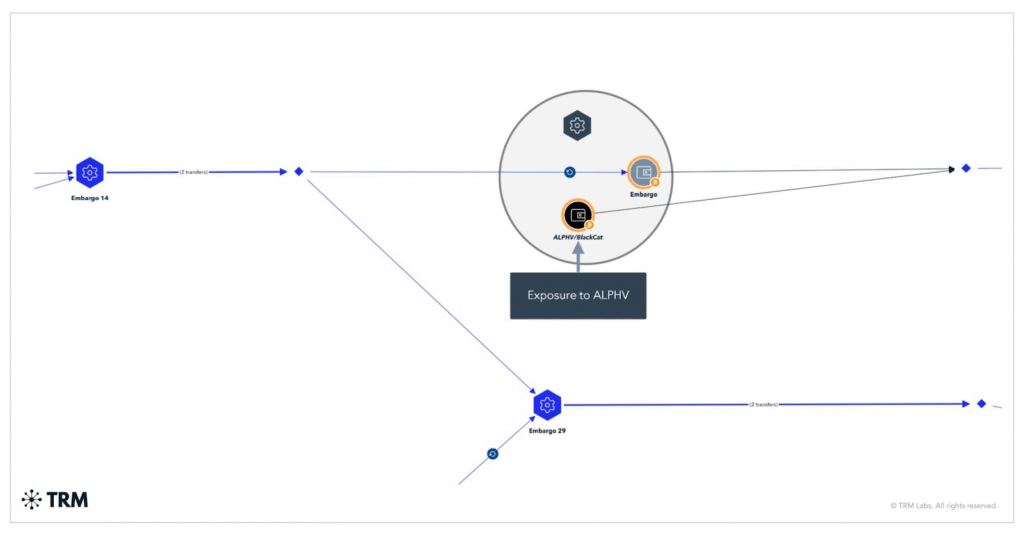
Both share technical traits, such as the use of the Rust programming language, a similar leak site design, and overlapping cryptocurrency wallet activity. These links point to an operation with roots in a well-resourced and experienced predecessor.
The group operates under the RaaS model, providing affiliates with attack tools while controlling infrastructure and ransom negotiations. This allows Embargo to scale operations quickly and maintain leverage in every deal. Affiliates gain reach, while Embargo ensures a consistent structure for its campaigns.
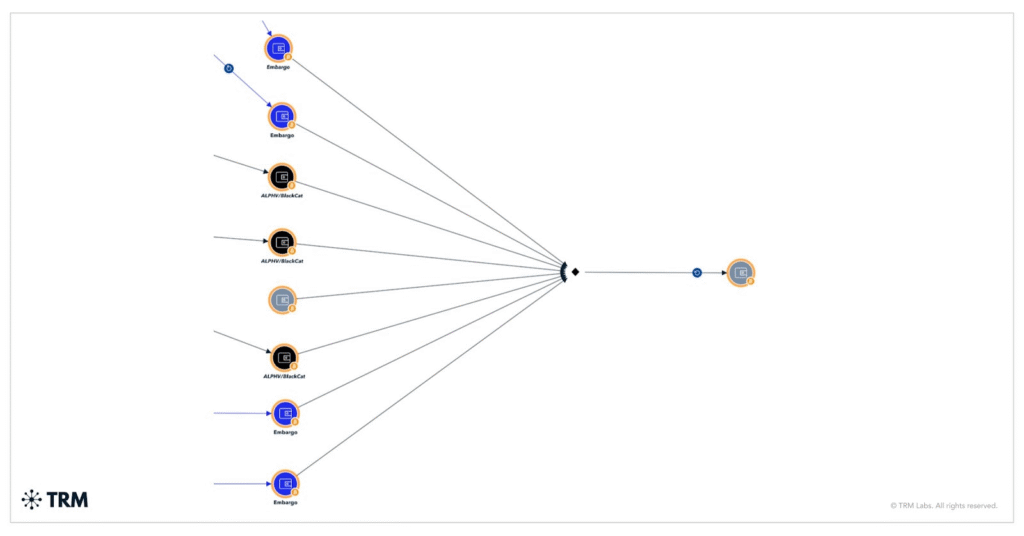
Crypto drives Embargo’s ransomware model
Embargo shows high technical skill. It disables security measures and removes recovery options before encryption. Entry often comes through unpatched software or social engineering schemes, such as phishing emails. Victims must communicate through Embargo’s channels, giving the group full control over ransom talks.
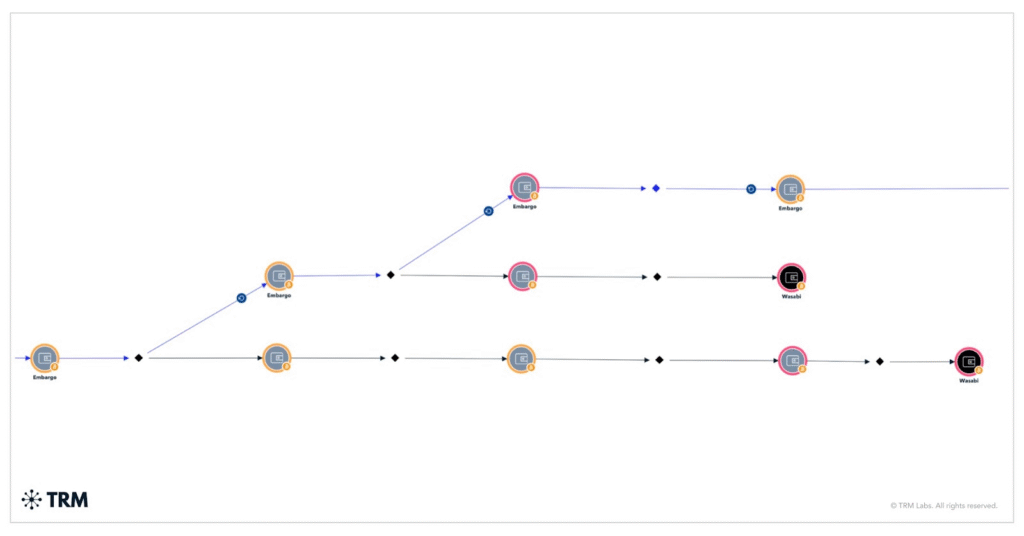
The group also uses double extortion, encrypting files while stealing sensitive data. If payment fails, it leaks or sells the data, increasing both reputational and regulatory damage for victims. Laundering tactics are calculated.
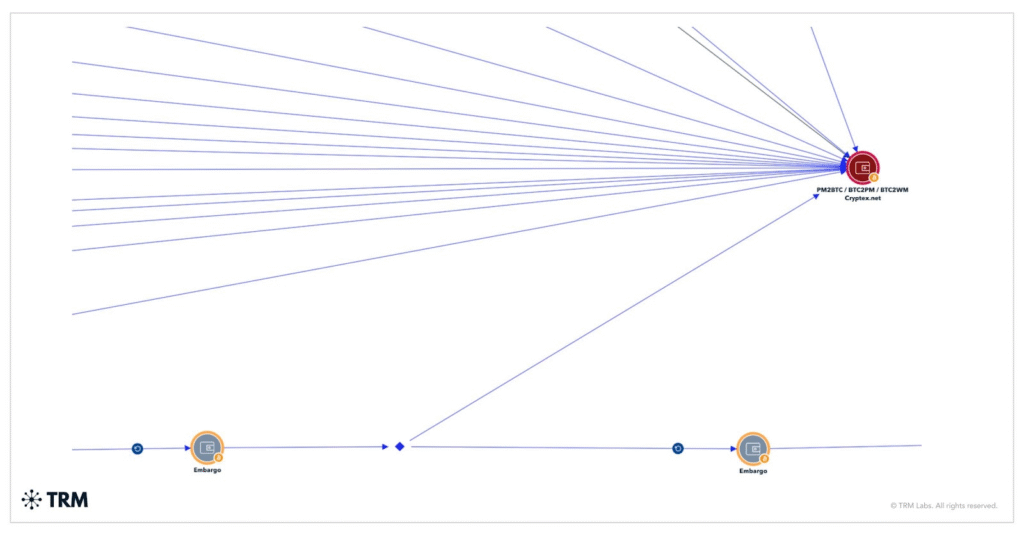
Embargo moves funds through intermediary wallets, high-risk exchanges, and sanctioned platforms like Cryptex.net. About USD 18.8 million sits idle in unattributed wallets, likely as a strategy to disrupt tracking or wait for more favorable conditions.
The group rarely uses mixers heavily, preferring layered wallet transactions to obscure activity. Cryptocurrency is central to its business model. Bitcoin remains the main choice, though privacy coins like Monero appeal to groups seeking stronger anonymity.
US faces the most Embargo Ransomware attacks
Law enforcement has increased tracing efforts, but Embargo adapts by evolving payment channels and laundering methods. The group’s focus on healthcare targets is notable. Such organizations face high pressure to restore operations quickly, making them more likely to pay.
In Europe and Asia, attacks occur less often, but the US remains the main hunting ground. While money is the main driver, some attacks have carried political messages.
This mix raises the possibility of state links, reflecting a growing trend where financial and geopolitical motives overlap. Embargo’s strategy of technical precision, subdued public presence, and targeted disruption makes it one of the most dangerous ransomware threats to emerge in recent years.