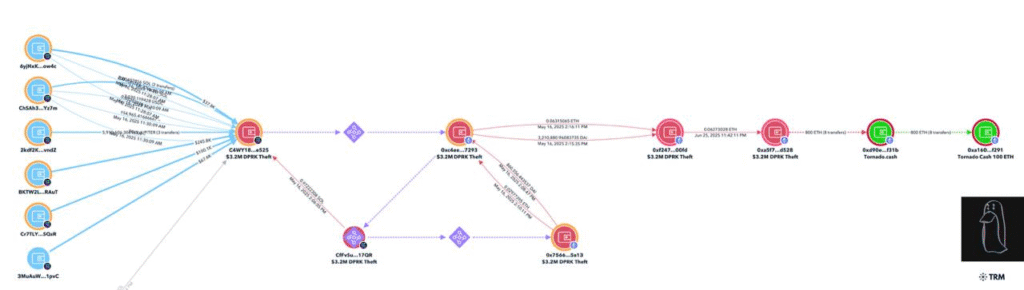
Hackers linked to North Korea’s Lazarus Group have moved $1.95 million in stolen crypto through Tornado Cash. Blockchain investigator ZachXBT traced the funds after a May 16, 2025, theft involving multiple Solana addresses. The hackers drained $3.2 million from a single victim.
After the theft, they converted the assets and bridged them to Ethereum. They sent 800 ETH to Tornado Cash in two rounds. The first batch of 400 ETH went in on June 25. Two days later, they sent the remaining 400 ETH.
The use of the mixer helps hide the origin and path of the funds. This makes tracking much harder for analysts and law enforcement. ZachXBT shared details and wallet addresses through his Telegram channel.
Lazarus used phishing and exploits
The hacker-controlled Ethereum wallet still holds around $1.25 million in DAI and ETH. That amount remains idle for now. The address on Solana linked to the theft is “C4WY1.” The one holding the leftover funds on Ethereum is “0xa5f.”
The Lazarus Group has a long history of targeting crypto platforms. It has stolen billions since 2018. The group funds North Korea’s missile and nuclear projects using proceeds from hacks. They carry out attacks using phishing, ransomware, and exchange exploits. U.S. authorities have sanctioned the group and tools like Tornado Cash.
Tornado Cash uses smart contracts to break the link between sender and receiver. This function appeals to both privacy advocates and criminals. It adds major challenges for tracing efforts. Law enforcement and analysts rely on transparent blockchains. Mixers reduce that transparency.
Crypto hackers use Cross-Chain moves
Cross-chain transfers like this one further complicate the picture. Funds hop between networks before landing on Ethereum. This flow helps hackers delay detection and move value. Tornado Cash then cuts the visible trail entirely.
Investigators will likely keep an eye on the idle $1.25 million. If moved, it could offer more clues or spark fresh alerts. Until then, it sits in a flagged wallet. The stolen funds remain partly hidden and partly exposed. The Lazarus Group shows no sign of slowing down.
Each attack adds urgency for global regulators and security firms. Tracking them across chains grows more complex each year. Despite these challenges, blockchain forensics still finds cracks in their cloak.